FormBook - Hiding in plain sight
published 2019-05-02
Intro
Today I came across the FormBook malware and had a quick look. As is tradition for malware, it uses encrypted strings to make it harder to detect. The way FormBook stores its encrypted strings however is new to me.
FormBook itself is not new and the decryption has been documented before and decryption scripts for its encrypted strings exist.
Arbor for example has an article here, and the decryption script which is basically a Python conversion of the code in FormBook itself can be found here.
Under the hood
So what does it look like in the binary?
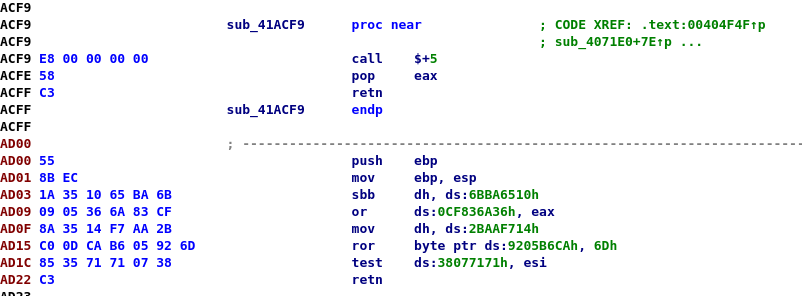
What you see here is an encrypted string blob. The lower part starting with push ebp is the actual string, while the top part is used to fetch its address.
Any string FormBook uses is stored in gibberish code blocks like above.
I've analyzed the function processing those code blocks but couldn't identify it at first. I expected some decompression/decryption but it looked like nothing I've seen before and it also seemed rather simple (just copying memory around basically). The existing script is also just a 1:1 translation of the malware's code into Python, so that doesn't solve the riddle either.
Then I had an idea - could it be that the processing code is actually a small disassembly engine? Turns out the answer is yes!
What FormBook actually is doing is disassembling these gibberish code blocks and extracts operands, which make up the "hidden" encrypted blob. So the weird transformation functions are part of the disassembly engine.
To confirm that, I ripped the above blob into a file and ran it through Arbor's script and printed the data before it is being decrypted using RC4, and the output was:
1065ba6b366a83cf14f7aa2bcab6059271710738
That is, these bytes are what are hidden in the code blob. And if you look closely, you can see the bytes in the above disassembly as operands but reversed (little-endian of DWORDs):
1065ba6b -> 0x6BBA6510
366a83cf -> 0xCF836A36
14f7aa2b -> 0x2BAAF714
cab60592 -> 0x9205B6CA
71710738 -> 0x38077171
So FormBook is literally hiding the encrypted strings in plain sight - as operands for nonsense code blobs and uses a small disassembly engine to retrieve them. Haven't seen this one before, that's a rather creative approach.
(I couldn't find anyone else noticing what's actually going on, so if I missed it, apologies, let me know)